A clean APK report, typically from a multi-engine scanner service like Virus Total, looks overwhelmingly green and uneventful. Its defining characteristic is a detection ratio of 0 against a long list of security vendors (e.g., 0/70), indicating that no antivirus engine has flagged the file as malicious. Beyond this primary score, a truly clean APK report will feature a valid digital signature that matches the legitimate developer, a list of requested permissions that are reasonable and logical for the app’s functionality, and a lack of suspicious behaviours or indicators in its detailed analysis sections. It’s a picture of digital normalcy, showing no signs of tampering, malware, or privacy-invading overreach.
H2: Why You Should Care About APK Reports

In the world of Android, sideloading—installing apps from outside the official Google Play Store—offers incredible freedom, but it comes with a crucial responsibility: you become your own security chief. Every APK file downloaded from a third-party store, a developer’s website, or a forum is an unknown quantity. It could be the legitimate app you want, or it could be a Trojan horse carrying malware, spyware, or adware.
This is where an APK analysis report becomes your most essential tool. Services like Virus Total, Meta defender Cloud, and others act as an impartial, multi-opinion security council. They take the APK file you provide and run it through dozens of different antivirus engines and analysis tools. The resulting report is a comprehensive security profile of the file, giving you the data needed to make an informed decision about its safety. Learning to read and understand this document is the single most important skill for any Android enthusiast who ventures beyond the walled garden of Google Play.
H2: The Anatomy of a Clean APK Report: A Deep Dive
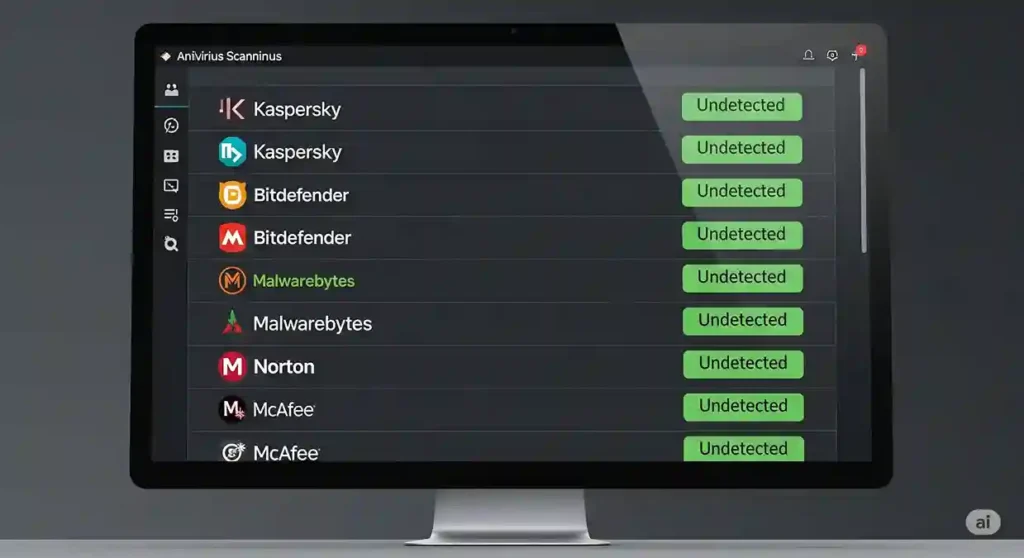
An APK report can seem daunting at first, filled with technical jargon and data points. However, they are structured logically. Let’s break down the key sections of a typical report, using the popular service VirusTotal as our primary example, to understand what to look for.
H3: The Detection Tab: The At-a-Glance Verdict
This is the first and most crucial section you’ll see. It provides the top-line summary of what the world’s leading antivirus engines think of the file.
H4: The All-Important Detection Ratio
The most prominent feature of the detection tab is the detection ratio, displayed as a fraction like 0/70.
- What it means: The first number is the count of security vendors that flagged the file as malicious. The second number is the total number of vendors that scanned the file.
- What a clean report looks like: For a clean APK report, this must be 0. A result of 0/70, 0/68, or similar is the gold standard. It signifies a consensus among dozens of security experts that the file contains no known threats.
- What about one or two detections? While a 0 is ideal, you might occasionally see a 1 or 2. This can sometimes be a false positive, where a scanner’s heuristic analysis is overly aggressive. However, you should treat any detection with suspicion. Investigate which specific vendors flagged it and what they named the threat. If reputable names like Kaspersky, Bitdefender, or Malwarebytes flag a file, it’s best to avoid it, even if others don’t. A truly clean APK report has zero ambiguity.
H4: The List of Security Vendors
Below the ratio, you’ll see a complete list of all scanning engines and their individual results. In a clean report, this list will be a sea of green Undetected or Clean results. It’s reassuring to scroll through and see dozens of trusted names giving the file a clean bill of health.
H3: The Details Tab: Verifying Authenticity and History
If the Detection tab gives the all-clear, the Details tab is your next stop. This section helps you verify the file’s identity and authenticity. A virus-free file can still be problematic if it’s not from the developer it claims to be.
H4: Signature Information: The Digital Fingerprint
This is one of the most underrated but critical parts of a clean APK report. Every legitimate Android app is signed with a developer’s digital certificate. This signature acts as an unforgeable seal.
- What it means: It proves who the developer is and verifies that the file has not been altered or tampered with since it was signed.
- What a clean report looks like: The report will show that the signature is Verified. It will display the certificate’s owner information (the developer’s name, e.g., Google LLC ). When you scan an APK for an update to an app already on your phone, you should verify that this signature information matches the original app’s signature. If an app claims to be an update to WhatsApp but the signature owner is CoolModder123, you are looking at a tampered and dangerous file, not a clean APK report.
H4: File Hashes (MD5, SHA-1, SHA-256)
These are unique fingerprints for the file itself. You can use these hashes to search for other reports or discussions online about this specific file, ensuring the file you have is the exact one others have analyzed.
H4: Basic Properties and History
This area shows details like file size, type, and importantly, the first and last submission dates to the scanning service. If a file was first seen years ago and has consistently produced clean reports, it adds a layer of confidence.
H2:Deciphering the Permissions and Behavior Tabs

Beyond the simple is it a virus? check, a sophisticated user must delve deeper into what the app does. This is where the Permissions and Behavior tabs of an analysis report become your magnifying glass for privacy and security risks. A file can be technically clean of malware but still be a privacy nightmare, and a thorough clean APK report analysis involves scrutinizing these aspects. The Permissions tab lists every single permission the app will request upon installation. Your job here is to apply context and common sense. A simple calculator app requesting android.permission.READ_CONTACTS, android.permission.SEND_SMS, and android.permission.ACCESS_FINE_LOCATION is a screaming red flag. There is no logical reason for a calculator to need this level of access. A truly clean report shows a permissions list that is lean and directly corresponds to the app’s advertised features. A mapping app will need location access; a photo editor will need storage access. The key is the Principle of Least Privilege (PoLP)—the app should only ask for the bare minimum permissions it needs to function. Anything more is suspicious and could be a sign of data harvesting.
The Behavior tab, if available, gives you an even more intimate look into the app’s soul. It details the app’s actions when run in a sandboxed environment. This section can reveal network connections the app attempts to make, files it tries to read or write, and services it starts. For a clean APK report, the network activity should be logical. An offline game that attempts to connect to dozens of unknown IP addresses in Russia or China is highly suspect. It should connect only to expected domains, such as its developer’s server for high scores or an ad network it discloses. Similarly, the report may show interesting strings found within the APK’s code—fragments of text. While often benign, you should look for suspicious strings like URLs to known ad-serving sites, commands like getroot, or references to exploit names. An app’s behavior should be predictable and boring. Any surprises, like attempts to access system files or communicate with strange domains, immediately tarnish the clean status of the report, even if no antivirus engine flagged it as a direct threat. This deeper analysis transforms you from a simple virus checker into a true security auditor.
H2: Putting It All Together: A Checklist for a Clean APK Report

To simplify the process, here is a step-by-step checklist to consult when you’re staring at a report and need to make a go/no-go decision.
H3: The Non-Negotiables (Red Flags)
If you see any of these, stop immediately. The file is not safe.
- Any Confirmed Detections: More than 1-2 detections, especially from major vendors (Kaspersky, Bitdefender, ESET, Symantec, Malwarebytes, Google).
- Invalid or Mismatched Signature: The signature status is Unverified, or the owner name doesn’t match the known developer of the app.
- Permissions for Device Administration: The app requests Device Administrator privileges for no good reason. This permission is extremely powerful and can make an app very difficult to uninstall.
H3: The Signs of a Genuinely Clean Report (Green Flags)
These are the positive indicators you are looking for.
- 0 Detections: A detection ratio of 0/XX is the primary goal.
- Verified, Matching Signature: The signature is valid and the developer name is who you expect it to be.
- Reasonable Permissions: The list of requested permissions aligns perfectly with the app’s features. Nothing is excessive or out of place. This is a hallmark of a properly compiled clean APK report.
- Normal Behavior: The behavioral analysis shows no strange network connections, no attempts to access sensitive system files, and no suspicious packed or obfuscated code.
- Community Score: Services like VirusTotal include a community score where users can vote if they think a file is harmful. A high number of harmless votes adds another layer of confidence.
H2: What a Clean Report Can’t Tell You
It’s crucial to understand the limitations of even the most detailed analysis report.
- Zero-Day Vulnerabilities: The report is based on what is known today. A brand-new, sophisticated threat might not be detected by any engine yet. This is rare, but possible.
- The App’s Intent: An app can be malware-free but still be poorly coded, unstable, or from a developer who will later sell your data. The report analyzes the file, not the developer’s ethics.
- Vulnerabilities in App Logic: The report won’t necessarily find security flaws in the app’s own code. For example, the app might store your password in an insecure way on your device. The APK itself is clean, but the app’s practices are not.
This is why your analysis of the report should be combined with good judgment. Sourcing your APKs from reputable places, like the developer’s official website or trusted open-source repositories like F-Droid, is just as important as scanning the file itself.
H2: Conclusion: Your Report, Your Verdict
Ultimately, a clean APK report is more than just a 0/70 score. It’s a comprehensive story that the file tells about itself. It’s a story of authenticity, confirmed by a valid digital signature. It’s a story of transparency, told through a reasonable list of permissions. And it’s a story of predictable behavior, demonstrated through normal network and file activity.
Learning to read this story is what empowers you to sideload with confidence. By moving beyond the simple detection score and scrutinizing the details of the signature, permissions, and behavior, you transition from a hopeful user to an informed gatekeeper of your own device’s security. The report provides the data; you provide the final, crucial judgment.
H2: What Have You Found in APK Reports?
Have you ever scanned an APK and been surprised by the results? What’s the most suspicious permission you’ve ever seen an app request? Share your experiences and tips in the comments below! If this guide helped you, please pass it along to others who might benefit from safer sideloading.






