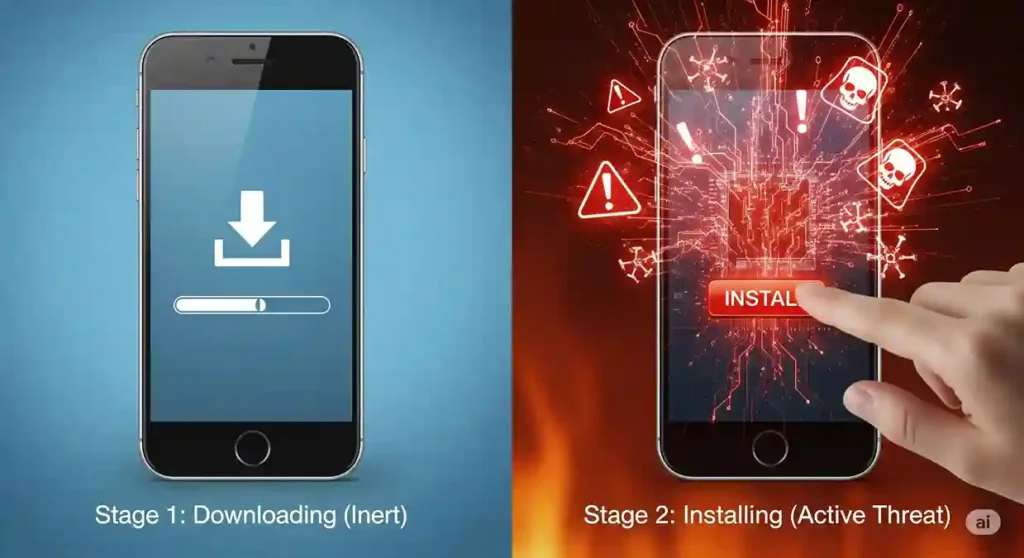
Technically, the simple act of downloading an APK file, in and of itself, is highly unlikely to infect your device with a virus. The file is merely transferred to your device’s storage, where it remains dormant and inactive, like a letter in an envelope. However, this is only half the story, and a dangerously misleading one at that. The real, potent threat materializes the moment you tap “Install.” The distinction between downloading a file (receiving the envelope) and executing it (opening and acting on its contents) is the absolute bedrock of your digital security. So, while you probably won’t get a virus from just downloading an apk file, the download is the first critical step in a process that can, and often does, lead to a full-blown infection that can compromise your entire digital life.
This article will serve as your definitive, in-depth guide to understanding the profound risks associated with APK files. We will dissect the fine line between downloading and installing, explore the sophisticated methods attackers use, examine real-world disasters, and ultimately equip you with the expert-level knowledge to keep your Android device secure in an increasingly hostile digital landscape.

The Critical Distinction: Understanding Downloading vs. Installing
Many users, in their haste to get a new app or game, conflate downloading and installing into a single, seamless action. This is a fundamental misunderstanding that cybercriminals eagerly and successfully exploit. To truly grasp the risks involved, you must visualize them as two distinct and separate events, one relatively benign and the other fraught with peril.
Stage One: The Download (The Passive Transfer)
When you click a link to download an APK file from a website, your browser or download manager initiates a simple data transfer. It fetches the package of data from the web server and saves it onto your phone’s local storage, typically within the “Downloads” folder.
What is the File Doing? Is It a Threat at This Stage?
At this point, the file is essentially inert. It is a dormant collection of code and resources. Think of it as a locked and sealed box containing a complex set of instructions and tools. You have successfully brought this box into your house, but you have not yet opened it, looked at the instructions, or used any of the tools. The code within the APK is not running. It is not interacting with your Android operating system, it cannot see your other apps, and it has no access to your personal data. In this dormant state, the file cannot:
- Access your contacts, call logs, or SMS messages.
- Activate your microphone or camera to spy on you.
- Install other malicious software or adware.
- Encrypt your photos and files for ransom.
- Connect to a remote server to exfiltrate your data.
Therefore, the direct answer to “Can you get a virus from just downloading an apk file?” leans heavily towards no, because the download phase is entirely passive. The file is self-contained and has not been given any permissions to act. An exception to this would require an incredibly sophisticated attack exploiting a deep, unpatched vulnerability in the Android Download Manager or media scanner itself—a scenario that is exceedingly rare for the average user.
Stage Two: The Installation (The Active Execution)
This is the moment of truth, the point of no return. When you navigate to your “Downloads” folder, locate the APK file you just saved, and tap on it to begin the installation process, you are actively giving the Android operating system the command to “unlock the box.” The system begins to unpack the file and execute the code contained within. This is where you are presented with the most critical security checkpoint in the entire process: the “Permissions” screen. It is a checkpoint that, unfortunately, most users treat as a simple roadblock, hastily clicking “Accept” or “Allow” to get to their app faster.
The Point of Infection: Granting the Keys to the Kingdom
By tapping “Install” and subsequently accepting the permissions the application requests, you are granting it legal authority (within the rules of the operating system) to perform specific actions. A legitimate calculator app might ask for no permissions at all. However, a malicious calculator app might ask for access to your contacts, SMS messages, storage, location, and camera. If you grant these permissions, you have personally and explicitly invited the virus into your device. You’ve given it the keys to your house, the combination to your safe, and a map to your most valuable possessions. The infection doesn’t happen by hacking in the cinematic sense; it happens through a user-authorized process. This is the crucial moment where the potential danger of a downloaded file becomes a kinetic, active threat.
H2: What Exactly Is an APK File? A Deeper Look
To understand the threat, we must first understand the package it arrives in. APK stands for Android Package Kit (or sometimes Android Application Package). It is the standard file format the Android OS uses for the distribution and installation of mobile apps and middleware.
The APK as a Digital Container
Think of an APK file as a more specialized version of a ZIP archive or a Windows .exe installer, but created specifically for the Android ecosystem. It’s a compressed bundle that contains all the essential elements an application needs to be installed correctly on a device. When you look inside an APK, you find a structured collection of files and folders:
- classes.dex: These are the compiled code files, written in Java or Kotlin, that contain the core logic of the application. This is where malicious instructions hide.
- res/: A folder containing all the app’s resources, such as images, audio files, icons, and layout designs.
- lib/: This directory includes compiled code that is specific to the device’s processor architecture (e.g., ARMv7, x86).
- assets/: A folder for raw asset files that developers can bundle with the app.
- META-INF/: This directory contains the application’s digital signature and a list of all its resources. The signature is used to verify the integrity of the package and prove who the developer is. Tampering with an APK breaks its original signature.
- AndroidManifest.xml: This is arguably the most important file from a security perspective. It is a mandatory file in every APK that acts as the app’s passport. It declares the app’s name, version, components, and, most critically, the permissions it requires to run.
When you download an app from the Google Play Store, your phone is still downloading and installing an APK file. The crucial difference is that Google acts as a trusted gatekeeper. The Play Store uses a sophisticated security suite, including Google Play Protect, to scan these files, verify developer identities, and analyze app behavior to vet them for malicious code before they are ever listed for download. When you “sideload”—the term for installing an APK from any source outside the official store—you bypass this entire security apparatus and become your own, sole security guard.
The Dark Side: How Malicious Code Infiltrates APK Files
Cybercriminals don’t always need to be brilliant programmers capable of writing malware from scratch. They are often just cunning manipulators who use simple, brutally effective techniques to trick unsuspecting users. The journey of how a safe, popular app becomes a weaponized Trojan is a frightening look into the cybercrime economy and directly relates to how you can get a virus from just downloading an apk file and then proceeding with the installation.
The “Repackaging” Ploy: A Trojan Horse Strategy
This is the most common and insidious method. An attacker targets a popular, legitimate application—let’s say a well-known game, a premium photo editor, or a useful productivity tool. They download the official APK. Using freely available tools, they decompile the original APK, which essentially unpacks it into its readable components. They then carefully inject their own malicious code (the “payload”) into the app’s source code. Finally, they recompile it into a new, weaponized APK. Since they have altered the code, they cannot use the original developer’s digital signature. Instead, they sign it with their own, new certificate. They then upload this “repackaged” app to third-party app stores, forums, torrent sites, or Telegram channels.
The Alluring Bait: “Pro,” “Unlocked,” “Ad-Free,” or “Modded”
The repackaged app is almost always advertised as something better than the original. The titles are designed to prey on user desire and the reluctance to pay for software. You will see them labeled as:
- A “cracked” version of a popular streaming app that promises to remove all ads and unlock the highest quality tier.
- A “modded” version of a popular online game that offers cheats like aimbots, unlimited in-game currency, or wallhacks.
- A “pro” version of a creative application with all expensive, paid-for filters and features unlocked for free.
This lure is incredibly powerful and effective. Users who search for these terms are actively looking for a shortcut and are more likely to ignore security warnings. They download the tampered APK, believing they’ve found a clever way to get premium features for free. In reality, they are installing a Trojan horse. The app might function perfectly, providing the promised features as a disguise, while the malicious payload runs silently and invisibly in the background, executing its true, sinister purpose.
Malicious Apps Built From the Ground Up
In other, more brazen cases, the entire application is a complete sham from its inception. Attackers will build an app that purports to provide a very simple, common utility—a flashlight app, a QR code scanner, a file manager, a phone “cleaner” or “booster,” or even a simple wallpaper app. These apps are trivial to create and serve as a perfect cover for malware. The user installs what they believe is a harmless tool, but the app’s primary function is malicious from the start. It might be silently logging their every keystroke, stealing their banking credentials via a fake login screen, or subscribing them to fraudulent premium SMS services that drain their phone bill.
H2: Case Studies in Calamity: Real-World APK Malware Attacks
To truly comprehend the gravity of installing a malicious APK, it helps to move beyond the theoretical and look at real-world examples where millions of users were affected. These campaigns highlight the sophistication and scale of modern mobile threats.
Case Study: The “Agent Smith” Campaign
Named after the self-replicating antagonist from The Matrix, the Agent Smith malware campaign, discovered in 2019, infected an estimated 25 million devices, primarily in India and surrounding countries.
Modus Operandi
The attackers used the “repackaging” method described earlier. They took popular apps like WhatsApp, SHAREit, and Flipkart, injected a malicious payload, and distributed them through 9Apps, a third-party app store. The malware’s primary function was not to steal data directly but to replace legitimate, installed apps on a user’s phone with its own infected versions. It did this by exploiting known Android vulnerabilities and its own clever code. Once it replaced a legitimate app, like WhatsApp, it would serve malicious advertisements, taking credit for them to generate fraudulent revenue for the attackers. While its main goal was financial gain through ads, the framework was so sophisticated that it could have easily been adapted for far more dangerous activities like credential theft or surveillance. This case proves that even seemingly benign “adware” can be part of a massive, invasive operation.
Case Study: The “Gooligan” Trojan
Uncovered in 2016, Gooligan was a terrifying piece of malware that rooted devices and stole authentication tokens, ultimately breaching the security of over one million Google accounts.
The Infection Vector and Impact
Gooligan was hidden inside dozens of seemingly legitimate apps on third-party Android app stores. When a user installed one of these apps, the malware would communicate with a Command and Control (C&C) server. It would then download a rootkit, exploiting older Android vulnerabilities to gain complete, privileged “root” access to the device—the highest level of control possible. Once rooted, Gooligan stole the user’s Google account email and authentication tokens. These tokens are what allow you to stay logged into your Google services without entering your password every time. With these tokens, the attackers could access the user’s Gmail, Google Photos, Google Docs, and more. Their primary goal was to fraudulently install other apps from the Google Play Store on the victim’s behalf, writing positive reviews to boost their ratings. This campaign demonstrated a direct, large-scale breach of personal cloud data originating from a single malicious APK installation.
Sideloading and the Permission Problem: A Blank Check for Criminals
The entire conversation about whether you can get a virus from just downloading an apk file is fundamentally a conversation about the risks of sideloading. While sideloading has legitimate uses for developers testing apps or users accessing geo-blocked services, for the average person, it’s a minefield. The single greatest point of failure in this entire process is not a technical vulnerability but a psychological one: the user’s casual and dangerous handling of app permissions. When you install an app from the Google Play Store on a modern Android version, the system has become much more intelligent, often asking for permissions only when the app actually needs them (this is called “runtime permissions”). For instance, a photo editing app will only ask for access to your camera or storage the very first time you try to take a picture or open an image with it. This contextual request gives the user a chance to understand why the permission is needed. Malicious sideloaded apps, however, often subvert this. They frequently target older Android versions or use techniques to demand a massive list of highly dangerous permissions all at once, right at the beginning of the installation process.
This is the digital equivalent of a complete stranger knocking on your door, and before you even ask who they are, you hand them the master keys to your house, your car, the password to your computer, and the combination to your safe, simply because they promise to fix a leaky faucet for free. Users have been conditioned for years to click “Next,” “Agree,” and “Allow” without reading, just to get through the installation process quickly. A simple-looking game that asks for permission to read your SMS messages, access your full contact list, record audio, and make phone calls is waving a giant, blood-red flag. Why would a game ever need these? It’s because the game is a front. The malicious code wants to read your text messages to intercept two-factor authentication codes from your bank. It wants your contact list so it can spread itself via SMS to your friends and family. It wants to record audio to spy on your conversations. It wants to make unauthorized calls to premium-rate numbers that charge exorbitant fees directly to your phone bill. Granting these permissions is the active, explicit step that turns a dormant, downloaded file into a devastating and autonomous security breach. The malware doesn’t need to hack its way in; you hold the door wide open for it. This is why a moment of vigilance at the permission screen is infinitely more valuable than any antivirus software you could ever install. You are the final and most important line of defense.
Your Pre-Installation Security Checklist: Becoming Your Own Security Analyst
Since the true danger lies not in the download but in the installation, the most powerful protection you have is a robust and skeptical vetting process before you ever tap that “Install” button. If you absolutely must install an APK from a source other than the Google Play Store, you must stop thinking like a user and start thinking like a security analyst.
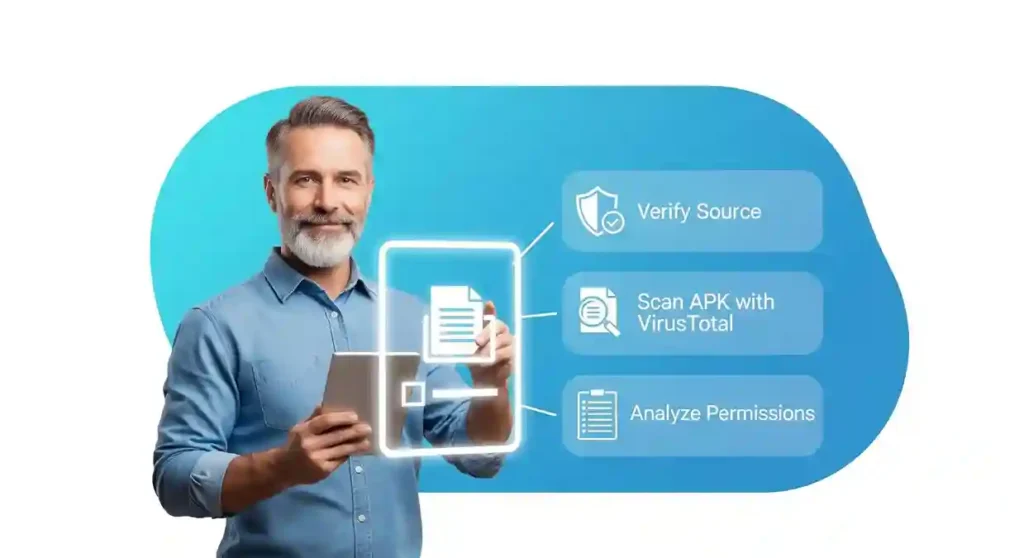
Rule #1: Scrutinize the Source with Extreme Prejudice
Where is this file coming from? Not all non-Google sources are equal.
- Relatively Safer: The official website of a well-known, reputable developer (e.g., downloading the Signal messaging app’s APK directly from the official Signal website). These developers have a reputation to protect. Another example is F-Droid, a repository dedicated to Free and Open Source Software (FOSS), which is generally considered much safer due to its transparent, community-vetted nature.
- Extremely Dangerous: A random link found in a forum post, a YouTube video description, a pop-up ad, a torrent site, or an unofficial “app market” that promises paid apps for free. If the source looks shady, it is shady. There is no such thing as a free lunch in the digital world; you always pay, often with your data and security.
Rule #2: Use a Multi-Engine File Scanner
Before the APK file ever has a chance to run, you can have it professionally analyzed. Do not install it first. First, upload the file itself to an online scanning service.
- VirusTotal: This is the industry standard and an indispensable tool. Owned by Google, VirusTotal allows you to upload the APK file you downloaded, and it will be scanned by over 70 different antivirus engines from companies like McAfee, Bitdefender, Kaspersky, and Malwarebytes. If even a handful of these engines flag the file as malicious, you should consider it toxic and delete it immediately.
- NVISIO ApkScan: A similar service that provides a detailed report on an APK’s potential threats, analyzing its code and structure for suspicious elements.
Rule #3: Read the Permissions Before Installation
You don’t have to install an app to find out what it wants to do. You can inspect the AndroidManifest.xml file’s permissions list beforehand.
- Use an APK Permission Viewer: There are apps and websites available that can analyze a downloaded APK file (without installing it) and show you a clear, easy-to-read list of all the permissions it will request.
- Apply the Principle of Least Privilege: This is a core security concept. A legitimate application should only ask for the absolute minimum set of permissions it needs to perform its stated function. A wallpaper app should never need access to your microphone. A calculator should never need access to your contacts. A QR code scanner should never need permission to make phone calls. If the permissions seem excessive or unrelated to the app’s function, it is almost certainly malicious.
Red Flags: How to Tell if Your Phone Is Already Infected
If you’ve recently sideloaded an APK and are now feeling a sense of dread, or if your phone has just started acting strangely, look for these common signs of a malware infection. Answering “yes” to several of these is a strong indicator of a compromise.
- Sudden and Severe Battery Drain: Malware, especially spyware and keyloggers, runs constantly in the background, consuming CPU cycles and, consequently, a lot of power. If your phone’s battery life suddenly plummets, it’s a major red flag.
- Unexplained Data Usage Spikes: Is your phone consuming significantly more mobile data or Wi-Fi than usual? The malware might be sending your personal files, photos, and logged data to a remote server controlled by the attacker.
- Sluggish, Unstable Performance: Your phone feels significantly slower than it used to. Apps take forever to load, the user interface stutters, and apps crash frequently for no reason.
- Aggressive and Intrusive Pop-Up Ads: You are being bombarded with ads in places you never saw them before, such as on your home screen, in your notification bar, or even interrupting your phone calls.
- New, Unrecognized Apps Appear: You see apps in your app drawer that you are 100% certain you never installed yourself. These could be “dropper” apps installed by the initial malware.
- Your Phone is Overheating: It’s normal for a phone to get warm when gaming or charging, but if it becomes unusually hot to the touch even when it’s idle, it’s a sign that a process is running out of control in the background.
- Suspicious Activity and Strange Bills: Your friends report receiving strange spam messages from your number or social media accounts. You see outgoing calls in your log that you didn’t make. Worse, your phone bill shows charges for premium SMS services you never subscribed to.
If you notice these symptoms, you need to act fast. Boot your phone into safe mode (which prevents third-party apps from running) and try to identify and uninstall the suspicious application. If that fails, the only guaranteed solution is a full factory reset, erasing everything on the device and restoring it to its original state.
Conclusion: Download with Awareness, Install with Extreme Caution
So, let’s return to the central question one last time: can you get a virus from just downloading an apk file? The purely technical answer, in over 99.9% of cases, is no. The download itself is a passive transfer of data. The file is a caged tiger. It may be dangerous, but as long as it remains in its cage on your download list, it can do no harm.
But the moment you tap “Install” and begin granting permissions, you are not just opening the cage door—you are personally unscrewing the hinges, disabling the alarms, and leading the tiger into your digital living room. The entire security model of sideloading rests squarely on the user’s shoulders. The powerful allure of getting something for nothing—a free premium app, a cheat in a game—is the bait used by criminals to convince you to willingly compromise your own security. By understanding the critical, monumental difference between downloading and installing, by treating every unknown source with suspicion, by meticulously scanning files before they run, and by reading every permission request with a critical eye, you can navigate the riskier parts of the Android world more safely.
For the vast majority of users, however, the safest, simplest, and most effective path is the one paved by Google: stick to the vetted, monitored, and protected ecosystem of the Google Play Store. The risk of venturing outside is rarely worth the reward.
What Are Your Experiences?
Have you ever sideloaded an app and had a bad experience, or do you have a success story about finding a great, safe app outside the Play Store? Do you have any other security tips for fellow Android users? Share your stories, questions, and advice in the comments below. Your experience could help someone else avoid a digital disaster.
And if you found this in-depth guide helpful, please share it on social media to help your friends and family stay safe!





